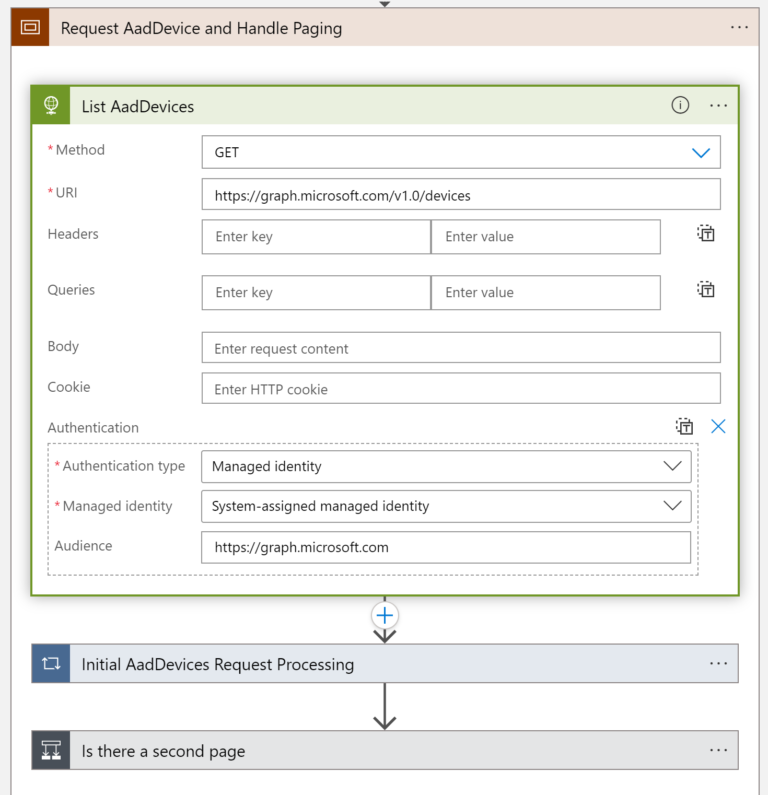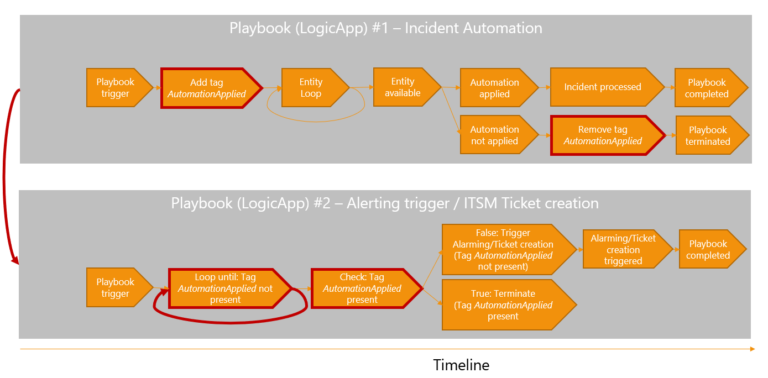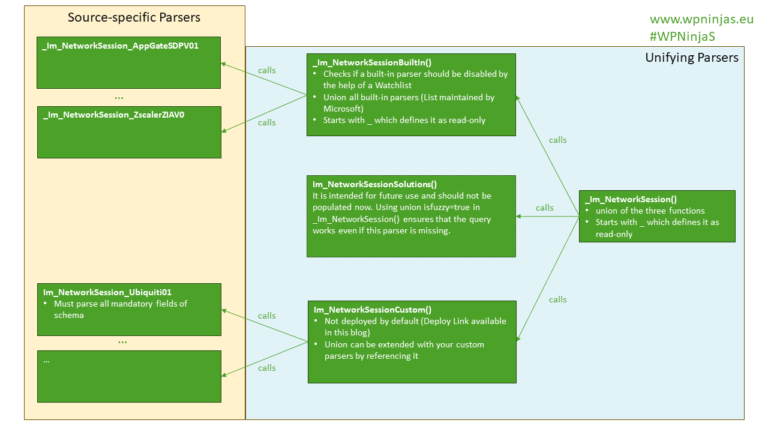
Microsoft Sentinel ASIM Parser demystified
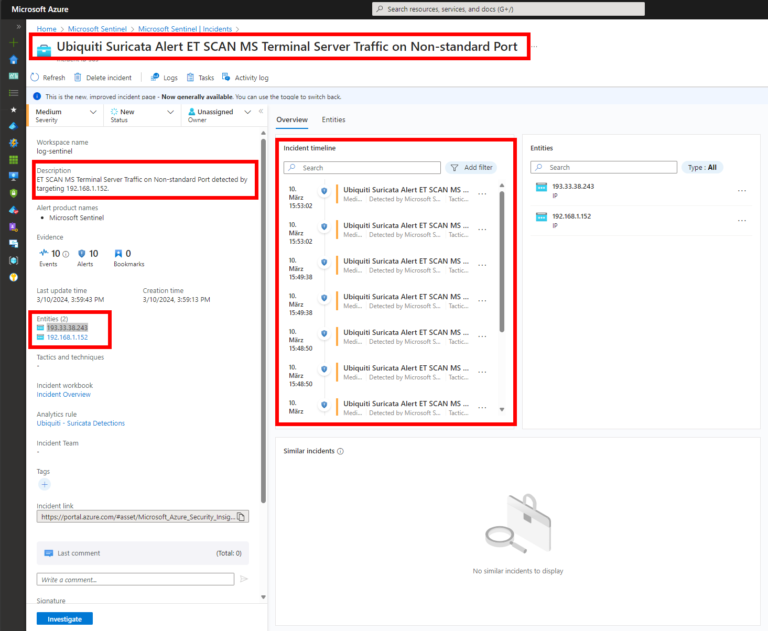
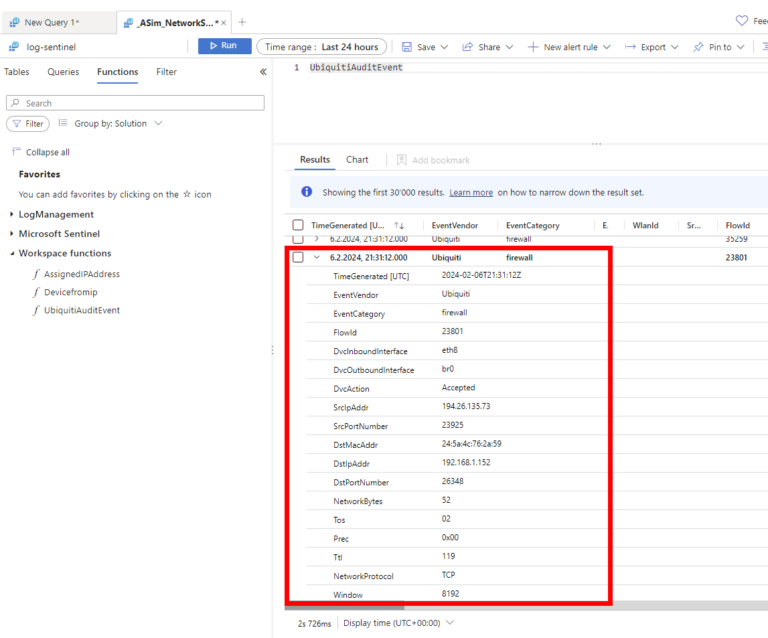
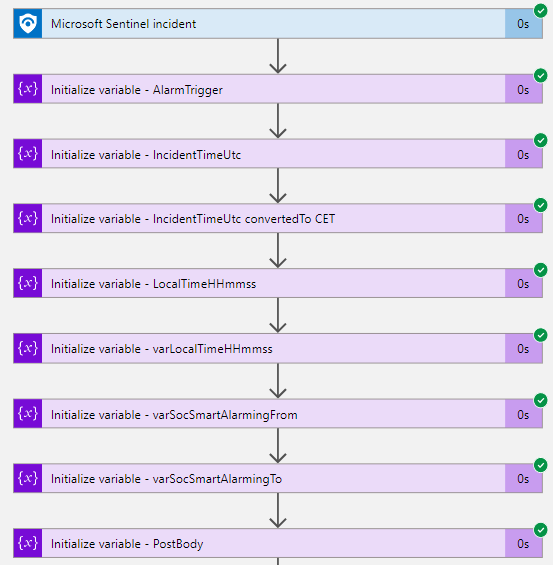
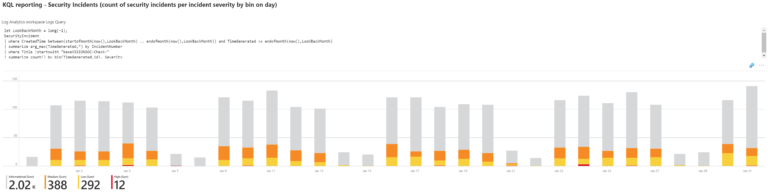
In the realm of cybersecurity, the ability to efficiently parse and analyze vast amounts of data is crucial. Microsoft Sentinel offers a powerful solution for this purpose. One of its key features is the ASIM (Advanced Security Information Model) parser, which plays a significant role in data normalization and enrichment.